“The CXO’s Guide to Advanced Persistent Threats: Insights from Ambisure Technologies!”
Every organization faces a significant threat through Advanced Persistent Threats (APTs) in our digital environment. Awareness of APTs holds particular importance for CXOs as protection of the corporate-assets and business continuity is their prerogative. Knowing What APTs are, Why are APTs a critical concern for CXOs, how can CXOs protect their organization from APTs, and what are the insights from Ambisure Technologies.
What is an Advanced Persistent Threat (APT)? & Reasons why APTs are most feared:
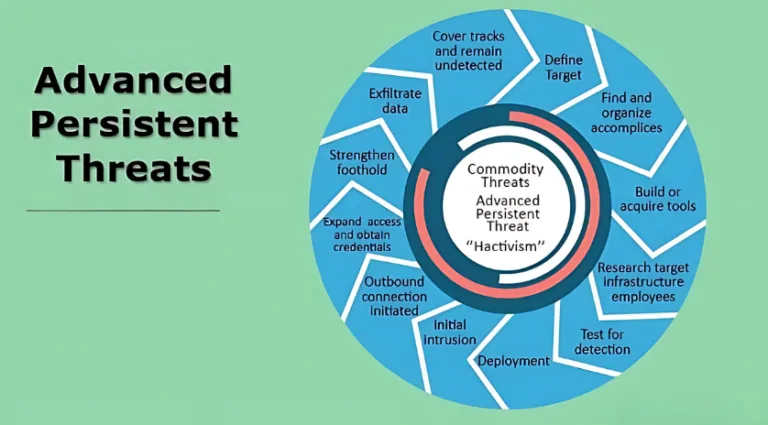
Fundamentally, an APT (Advanced Persistent Threat) is a long-term and targeted cyberattack where an intruder has been granted unauthorized access to a network that stays there, which is unnoticed for months at a time. APTs are extremely sophisticated, and are mostly used for stealing sensitive information or compromising critical infrastructure disrupting the business so reasons why are dangerous and feared:
- Long-term persistence: Attackers stay in the network for months and years at a time, learn about the organization and its IT infrastructure leading to apply exploitation methods.
- Methods: APTs combine methods like social engineering, malware, and other advanced techniques to penetrate systems, covering their tracks while extracting data, setup Command & control center outside the network.
- Targeted: Unlike most cyberattacks, APTs are targeted at specific high-value assets. APTs are meant to disrupt systems and company under the multiple motives of Espionage, Ransomware, Money, National Security, Revenge, Financial data etc.
Where traditional cyberattacks typically focus on rapid exploitation of well-known flaws, APTs operate differently. Instead, they fly under the scanning system, and are clever and hard to spot.
Why Are APTs a Critical Concern for CXO's ?
High Stakes & Financial Impact:
APT contravection can be extremely costly. In addition to immediate monetary losses, the harm done to an organization’s reputation, intellectual property and customer trust could leave behind its impact for years. CXOs should realize that APTs are directed at high-value assets which are critical for an organization’s survival or long-term development. Data breaches are getting more and more expensive, and APTs help to drive up that cost by stealing high-value information a little bit at a time continuously over a long period of time.
Evolving Threat Landscape:
Recent development of Cyber Security — The cyber criminals are evolving with the security technology too. APTs are highly developed, using AI, machine learning and automation to stay away from detection by standard security methods. Not monitoring the threat environment means an organization may become an easy victim for the advanced growth threats if CXOs have not been keeping watch.

Reputation and Trust:
CXOs will agree that the harm due to the reputation is the hardest hit to overcome. When APTs lead to agreements, the loss of customer trust and damage to brand image can be difficult to reconstruct. This could lead to regulatory penalties, legal expenses, and even this can reduce market share. So for CXOs, along with data security, preserving the reputation of their organization is equally important.
Compliance & Legal Risks:
The rising regulatory requirements from Regulators like RBI, SEBI, IRDA & Global Compliance requirements like HIPAA, FDA, PCI, GDPR, CCPA, and other data protection laws have put pressure on organizations to make sure that there is no breach in the security of the system and the data is protected. When an APT incident occurs these leads to multiple fines across different geographies, and also loss of business follows.
Operational Disruption:
APTs typically attack through malware which act in advance, using a specific insecurity that seizes operation functionalities. Hence, an organization may suffer from lost accesses to the critical systems, system downtime, or ransomware spreading within the business network. For CXOs, the importance of business continuity would be vastly threatened by APTs mainly because they completely disable an organization’s functional capabilities. For example, the critical systems may go down for days. The operational and financial impacts of the disaster may last for a longer time.
How Can CXOs Protect Their Organization from APT's ?
- Implement a proactive security approach:
Every organization faces a significant threat through Advanced Persistent Threats (APTs) in our digital environment. Awareness of APTs holds particular importance for CXOs as protection of the corporate-assets and business continuity is their prerogative. So for CxOs its important to Know What APTs are, Why are APTs a critical concern for CXOs, how can CXOs protect their organization from APTs, and you can always get some interesting insights from expert team of AmbiSure Technologies.
Instead of being reactive, they should make CXOs as the promoter of preventing strategies. This includes:
- Continuous Monitoring
- Threat Intelligence
- Follow Defense in Depth Strategy:
Because APTs tend to bypass traditional perimeter defenses, a collective & indepth security strategy is called for: for eg. for Endpoints protection following can be one way.
- Endpoint Detection and Response (EDR).
- Network Segmentation.
- Zero Trust Architecture.
This is just a starting point..
- Employee Training & Awareness:
The human element is often the weakest link in an APT attack, as social engineering tends to be the initial point of entry. CXOs should:
- Security Training Continuously: It gives regular training on how phishing and spear-phishing works.
- Simulated Phishing Tests:Simulated phishing tests are to be done to test employee awareness in handling suspicious emails and messages.
- Clear Incident Reporting Procedures: This train employees on how to quickly report suspicious activities.
- Management Awareness: Do Table Top Excercises to Train Management on how to respond to CyberIncidents.


- Incident Response & Recovery Plan:
A good IR plan is useful in reducing the consequences of a successful APT attack:
- IR Playbook: Establish and maintain a specific plan of what to do in case of an APT attack, so as to contain it as quickly as possible and recover it fast.
- Data Backups: Ensure that you regularly back up critical data and test your capacity for rapid restore in case of an cyber attack.
- Post-Attack Analysis: Make sure that, after an incident happens, that you conduct a comprehensive analysis of the mode of breach to build appropriate and corrective actions into the system to avoid such breaches again in the future.
5. Collaborate with Experts:
Cyber attacks are highly complex, and APTs continue to add composure each day. Working together with such experts like AmbiSure Technologies could be quite an revelation for you regarding your particular threat landscape, which will help you develop solutions to specifically fit that need.
Conclusion :
Hence we can conclude that Advanced Persistent Threats are in fact a business risk that demand executive attention. As a CXO, the role of cybersecurity strategy is critical for protecting the organization from loss of assets and degrading its reputation or moving forward. With the help of proactive security, technology investments and education for your teams, you can strengthen your resilience against APTs as well as make sure that your organization is secure in the continuously evolving threat landscape.
At AmbiSure Technologies, we are here to help your organization tackle these issues by protecting you against the most sophisticated cyber threats in today’s market.
Archives
- March 2025 (6)
- February 2025 (5)
- November 2024 (5)
- June 2024 (7)
- April 2024 (1)
- September 2022 (3)





















