The Importance of Network Security
- Network security is crucial in protecting sensitive data, preventing unauthorized access, and maintaining business continuity.
- A robust network security infrastructure ensures the confidentiality, integrity, and availability of information.
- Network security breaches can lead to financial loss, reputational damage, and legal repercussions.
- Breaches may result in data theft, disruption of services, and compromised customer trust.

Why do you need network security for your organization

Any network is vulnerable to malicious use and accidental damage unless it is properly secured. Private data, including trade secrets and customer information, can be exposed by hackers, disgruntled employees, or poor security practises within an organisation.
While hackers stealing customer information and selling it to be used in fraud generates negative publicity and public mistrust in the organisation.
Network security is any activity designed to protect the usability and integrity of your network and data.
- Includes hardware and software technologies
- Protection from Multiple Cyber threats
- Prevents malicious actors from entering and spreading on your network
- Effective network security allows authorized access to your network
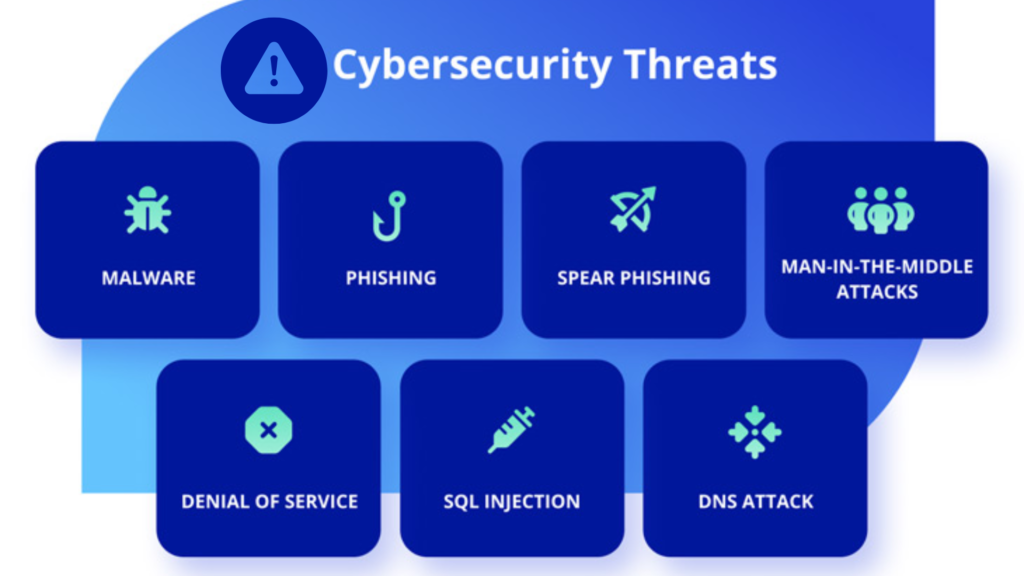
Types of cyber security threat & Cyber attacks
- Phishing Attack – Deceptive attempts to obtain sensitive information by impersonating a trustworthy entity through fraudulent communication.
- Malware & Ransomware – Malware is malicious software that infects systems to disrupt operations or steal information.
- DoS Attack – DoS attacks are malicious attempts to disrupt network availability by overwhelming resources with excessive traffic, rendering them inaccessible
- MIM Attack – Intercepting and altering communication between two parties without their knowledge or consent.
- SQL Injection – Exploiting vulnerabilities to inject malicious SQL code into a web application’s database queries.
- DNS Attack – Malicious activity targeting the DNS infrastructure, aiming to disrupt or manipulate domain name resolution.

Firewalls & Intrusion Detection Systems (IDS)
Firewalls and IDS are network security measures that monitor and control traffic, detect and respond to suspicious activities, and protect against unauthorized access and attacks.

Virtual Private Networks (VPNs)
VPN (Virtual Private Network) creates a secure, encrypted connection over a public network, allowing users to access private networks remotely while ensuring confidentiality and privacy.

Network Monitoring and Security Audits
Net Monitoring involves the cont-monitoring of net traffic, devices, & systems to detect & respond to sec incidents promptly. Sec Audits assess the effectiveness of security controls and identify vulnerabilities.
frequently asked questions
-
Securing your network will help protect the integrity of your firm’s data and better ensure that your systems are not breached. The good news is that there are clear ways to improve your network security and reduce the risk of attacks against your firm. Here are some of the methods you can implement
- a. Perform Auditing and Mapping
- b. Improve your Password Security
- c. Add a critical layer of protection
- d. Establish a backup plan to avoid data loss
- e. Keep the network up-to-date
- f. Physically secure the network
- g. Consider MAC address filtering
- h. Implement VLANs to segregate traffic
- i. Use 802.1X for authentication
- j. Use VPNs to encrypt select PCs or Servers
- k. Encrypt the entire network
- l. Educate your front line
- After all end-users have moved maximum of their activities to the Web, fraudsters have followed, devoting more of their attention to creating security threats based on Web applications.
- Network Security helps to protect your network while maintaining the confidentiality and integrity of Data flowing across the network as well ensuring the availability of critical Enterprise Assets.
- 90% of the attack vectors originate on a network level and malicious actors use underlying vulnerabilities to escalate across the network. Securing your Organization’s network infrastructure helps prevent a lot of these attacks hereby limiting the threats to the enterprise's assets.
- An effective, managed firewall will significantly reduce risk to your business. Without a firewall, your business could easily succumb to a cyber-attack, causing you to lose all of your important data. This would not only disrupt business processes, but would also reduce productivity and likely damage your reputation and brand.
- A properly configured, maintained, and monitored firewall will protect your data, network, and devices. Importantly, you need to ensure that your firewall has the power to manage normal and encrypted internet traffic without slowing down your devices or compromising security.
- The evolving tools, tactics and procedures used by cybercriminals to breach networks means that it’s important to regularly test your organization’s cyber security.
- VAPT helps to protect your organization by providing visibility of security weaknesses and guidance to address them. VAPT is a term used to describe security testing that is designed to identify and help address cyber security vulnerabilities. The meaning of VAPT can vary from one geographical region to another, either as a bracket for multiple distinct services, or a single, combined offering. VAPT as a whole could include anything from automated vulnerability assessments to human-led penetration testing and red team operations. click here to know more about VAPT tools provided by ambisure.
- Passive attacks: A Passive attack attempts to learn or make use of information from the system but does not affect system resources. Passive Attacks are in the nature of eavesdropping on or monitoring transmission. The goal of the opponent is to obtain information that is being transmitted.
- Active attacks: An Active attack attempts to alter system resources or affect their operations. Active attacks involve some modification of the data stream or the creation of false statements.