Data security solutions
The most effective method for finding, monitoring, and protecting sensitive data at scale.Reduce risk quickly, detect abnormal behaviour, and demonstrate compliance with the all-in-one data security platform that won't hold you back.
Why do you need it?
Data security is critical to public and private sector organizations for a number of reasons.
- There’s a legal and moral obligation for companies that have to protect the data of their users and customers so that it does not fall into the wrong hands.
- There’s also a risk of a data breach or hack which might harm your reputation. If you do not take data security seriously, your reputation can be permanently damaged in the event of a publicized, high-profile data breach or hack.
- Not to mention there are also financial and logistical consequences if a data breach occurs.
You’ll need to invest time and money to assess and repair the damage, determining which business processes have failed and what needs improvement.
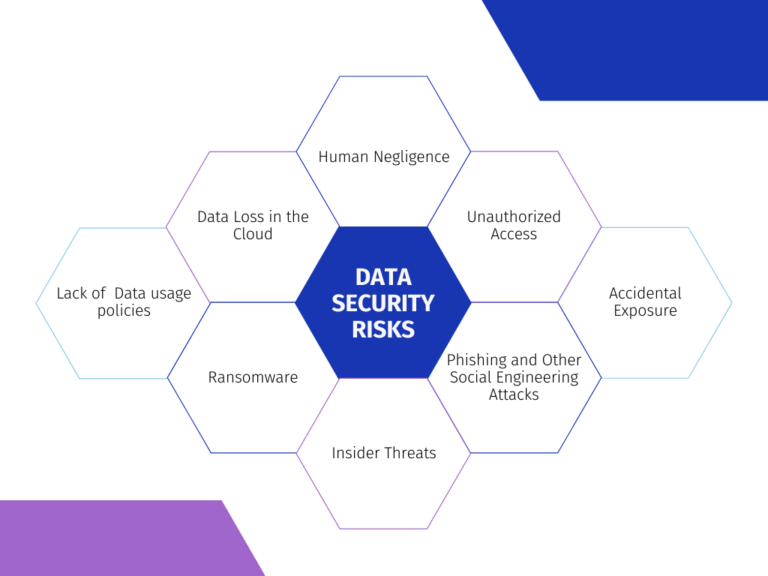
Data Security Risks
3 Ways a Data Security Breach
- Cost, fine, and reparations
- Reputational Damage
- Job Losses
How we can help Maintain Data Security for Businesses
- We Ensure Business Continuity
- We avoid Data Breaches
- We Prevent Unauthorized Access

What we Provide
QUERY
- Data Discovery and Classification
Data detection is the basis for knowing what data you have. Data classification enables the development of scalable security solutions by identifying which data is sensitive and must be protected. Data detection and classification solutions allow for file tagging on endpoints, file servers, and cloud storage systems, allowing you to visualise data across the enterprise and apply appropriate security policies.
- Data Loss Prevention (DLP)
Organizations can use a variety of protective measures to prevent data loss, including backing up data to another location. Natural disasters, outages, or attacks on local servers can all be mitigated by physical redundancy. Redundancy can be achieved in a local data center or by replicating data to a remote site or cloud environment.
- Governance, Risk, and Compliance (GRC)
- Data Security Audits
- Enterprise Data Rights Management (EDRM)
- EDRM is successful when it is combined with data classification and is integrated with file repositories and business applications.
- Anti-Malware, Antivirus, and Endpoint Protection
frequently asked questions
- Data security is a company’s protective measures put in place to keep any unauthorized access out of their databases, websites, and computers. Basically, this process offers a mechanism to protect data from corruption or loss.
- Whether you’re running a small or a big company, data security is very important and must not be overlooked so as to avoid any security breaches. That is the reason why one of the recommendations you should take into consideration is to implement data security solutions as soon as possible if you want to protect your company from cyber-attacks.
- When data that should be kept private gets in the wrong hands, bad things can happen. A data breach at a government agency can, for example, put top-secret information in the hands of an enemy state. A breach at a corporation can put proprietary data in the hands of a competitor. A breach at a school could put students’ PII in the hands of criminals who could commit identity theft. A breach at a hospital or doctor’s office can put PHI in the hands of those who might misuse it.
A data security policy specifies details about how customer data, employee PII, intellectual property, and other sensitive information is to be handled. Sometimes it is referred to as a “customer data security policy,” but the broader term “data security policy” is more accurate.
A data security policy should include two broad categories of elements: policies that apply to people, and policies that apply to technology.
People Elements of Data Security Policy
- Acceptable Use
- Passwords
- Auditing
- Social Networking
- Security Incident Reporting
Technology Elements of Data Security Policy
- System Security
- Mobile Device Management
- Vulnerability Scans
- Access Control Management and Monitoring
- Software Inventory, License Management, and Patch Management
- Backup, Recovery, and Disaster Recovery
You can ensure Data Security by following these 4 practices:
- Create a Risk-Aware Culture--Especially if Employees Use Their Own Devices
- Safeguard Passwords
- Secure Access Through System Administrators
- Make Your Cloud a Fortress
- Data integrity and data security are related terms, each playing an important role in the successful achievement of the other. Data security refers to the protection of data against unauthorized access or corruption and is necessary to ensure data integrity.
- That said, data integrity is the desired result of data security, but the term data integrity refers only to the validity and accuracy of data rather than the act of protecting data. Data security, in other words, is one of several measures which can be employed to maintain data integrity. Whether it's a case of malicious intent or accidental compromise, data security plays an important role in maintaining data integrity.