TPRM
Third-Party Risk Management (TPRM) is the process of analyzing and minimizing risks associated with outsourcing to third-party vendors or service providers.
There are many types of digital risks within the third-party risk category which include financial, environmental, reputational, and security risks.
Because vendors have access to intellectual property, sensitive data, personally identifiable information (PII), and protected health information, these risks exist (PHI).
The SIEM tools provide:
THE RISKS THAT A THIRD PARTY INTRODUCES?
SIEM works by combining two technologies:
a) security information management (SIM), which collects log data for analysis and reports on security threats and events, and
b) security event management (SEM), which conducts real-time system monitoring, notifies network admins about important issues and establishes correlations between security events.

THE RISKS THAT A THIRD PARTY INTRODUCES?

Cybersecurity risk:
The risk of being exposed or losing money as a result of a cyberattack, security breach, or other security incident. Cybersecurity risk is frequently mitigated through due diligence prior to vendor onboarding and continuous monitoring throughout the vendor lifecycle.

Operational risk:
The risk of a third-party causing disruption to the business operations. Service level agreements (SLAs) and business continuity and incident response plans are typically used to manage this. Depending on the vendor’s criticality, you may choose to have a backup vendor in place, which is common in the financial services industry.

Legal, regulatory, and compliance risk:
The possibility of a third party interfering with your compliance with local legislation, regulations, or agreements. This is especially critical for financial services, healthcare, and government organisations, as well as their business partners.

Reputational risk:
The possibility of negative public opinion as a result of a third party. Customers who are dissatisfied, inappropriate interactions, and poor recommendations are just the tip of the iceberg.

Financial risk:
The possibility that a third party will have a negative impact on your organization’s financial success. For example, your organization may not be able to sell a new product due to poor supply chain management.

Strategic risk:
The possibility that your company will fail to meet its business objectives as a result of a third-party vendor.
FEATURES AND CAPABILITIES:

Security Ratings
Security ratings, also known as cybersecurity ratings, are a data-driven, objective, and dynamic assessment of a company's security posture. They are developed by a reputable, independent security rating platform, making them useful as an objective indicator of an organization's cybersecurity performance. The higher the security rating, the better the security posture of the organisation.

Questionnaire Library
Today’s attacks are becoming more sophisticated, meaning organizations need equally advanced tools. Attackers frequently rely on compromised credentials or coerce users into actions that harm their organisation. SIEM tools, such as UEBA, should be equipped with machine learning capabilities to detect these threats more quickly. This allows for the monitoring of suspicious user behaviour from both internal and external threats.

Customizable Questionnaires
Look for a solution that includes a library of pre-built questionnaires to help you quickly assess your vendors' compliance with industry best practises and regulatory requirements.

Customizable Questionnaires
In addition to standard questionnaires, some organisations may wish to create their own security questionnaires based on their specific needs and desires.

Scalability and Automation
Not every solution will be able to provide the automation needed to rapidly scale and manage hundreds or even thousands of third parties. Nor does every solution provide the same level of coverage. If your company uses small specialist vendors, make sure the solution covers them.

Remediation Workflows
Based on automated scanning and completed questionnaires, a platform with remediation workflows will allow you to request remediation from a specific vendor. It will also allow you to view current remediation requests, the risks that have been requested to be remediated, and the date the remediation request was sent.

Reporting
It is critical to be able to report on the results of your third-party risk management programme to the Board, senior management, regulators, or colleagues. This is why a robust and simple-to-understand reporting capability is essential.

Fourth-Party Discovery
It's important to understand who your fourth-party vendors are. While you may not have a contractual agreement with them, they can still impact the confidentiality, integrity, and availability of your organization.

Continuous Monitoring
To stay ahead of new risks, you need a solution that is always up to date.

Accuracy and Thoroughness
Your third-party risk management program is only as effective as the data it relies on. If you use security questionnaires, try to use a well-tested template, and if you use security ratings, look for ones that follow the Fair and Accurate Principles.

ADVANTAGES OF TPRM:
- Cost reduction: It’s appropriate to think for third-party risk management as an investment. It costs money (and time) up front but saves money in the long run. A strong third-party risk management strategy can significantly reduce the likelihood of a data breach.
- Regulatory compliance: Third-party management is a core component of many regulatory requirements. Depending on your industry and the type of data you handle you may be legally required to assess your third-party ecosystem to avoid being held responsible for third-party security incidents. The truth is third-party risk management is now part of industry standards in most sectors and non-compliance is not an option.
- Risk reduction: Due diligence simplifies the vendor onboarding process while lowering the risk of third-party security breaches and data leaks. In addition to initial due diligence, vendors need to be reviewed on a continuous basis over their lifecycle as new security risks can be introduced over time.
- Knowledge and confidence: Third-party risk management improves decision-making across all stages, from initial assessment to offboarding, by increasing your knowledge and visibility into the third-party vendors you work with.
- ADDED BENEFITS:
- Improved security and customer trust
- Increased time savings
- Less redundant work
- Better data visibility and simpler assessments
- Faster vendor onboarding and better vendor performance
- Better reporting capabilities
- Easier audits and less spreadsheets

5 STEPS TO IMPLEMENT TPRM
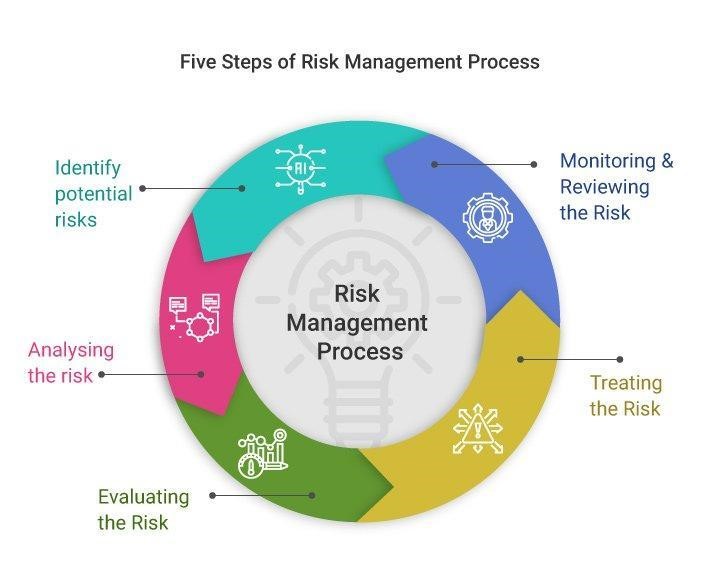
- Identify – The first step is to determine which companies you do business with that may pose a risk. Understanding the third-party ecosystem is essential.
- Classify – Using a risk-based approach, determine how much risk each third-party poses to your organisation based on data, system access, and service provided.
- Assess – Next, evaluate the security posture of third-party vendors with whom you do business. You will have varying levels of assurance based on third-party risk depending on the nature of your organization.
- Risk Management – Outline steps to put policies in place and decide how remediation should be handled. Essentially, you’re asking whether you should accept or avoid risks.
- Monitor – The final step is to continuously monitor third parties to ensure they are meeting contractual obligations and maintaining their security posture.

THE PROBLEMS TPRM HELPS IN MITIGATING
- Manage third-party processes throughout the relationship lifecycle
- Onboard third-party companies
- Perform third-party risk profiles and categorization
- Provide third-party assessments
- Provide third-party oversight and manage workflow
- Present reports and continuous updates
- Provide ongoing monitoring of critical third parties
QUERY
frequently asked questions
- Any non-University, outside entity, including non-profit groups and non-registered student organizations on campus (e.g., vendors, service providers, grant providers, unregistered fan clubs, unregistered student groups, and unregistered interest/support groups), can be classified as a third party.
- It is important to manage third-party risks to make informed risk decisions and comply with regulatory requirements. Failure to adequately manage third-party risk may increase UCLA’s exposure to operational risks, major personal data loss, financial losses, and significant, and adverse reputational impact.
- The Department/Unit engaging with the third party is accountable for managing the third-party relationship and associated risks. UCLA stakeholders such as OCISO, Campus Purchasing, Privacy, Accessibility Office, CRE, etc. perform additional risk assessment activities to assist the Unit with risk identification and mitigation.
- The responses to the UCLA Triage Form questions help to identify applicable risks and drive the subsequent risk management activities and third-party oversight requirements.
- The Third-Party Risk Assessment is used to review a third party’s ability to comply with UCLA’s data security expectations. The assessment reviews the third party’s controls related to data security, business continuity & disaster recovery, application security, network security, vulnerability management, etc. and identifies control gaps, as appropriate.
- When outsourcing services/products to a third party, it is important that risks arising from the outsourced activity are managed to prevent harm to UCLA.
- From the time of initiating a third-party request, it may take up to nine weeks to conduct triage, assess the third party, and review third-party contracts.