Multi Factor Authentication SECURE YOUR MOST CRITICAL APPS FIRST Multifactor Authentication is an authentication method that requires the user to provide two or more verification factors to gain access to...
KEEP YOUR PRIVILEGED USERS ALWAYS SAFE Privileged Access Management in a cybersecurity network consists of strategies and technologies for gaining control over privileged access and permissions for users, accounts, processes...
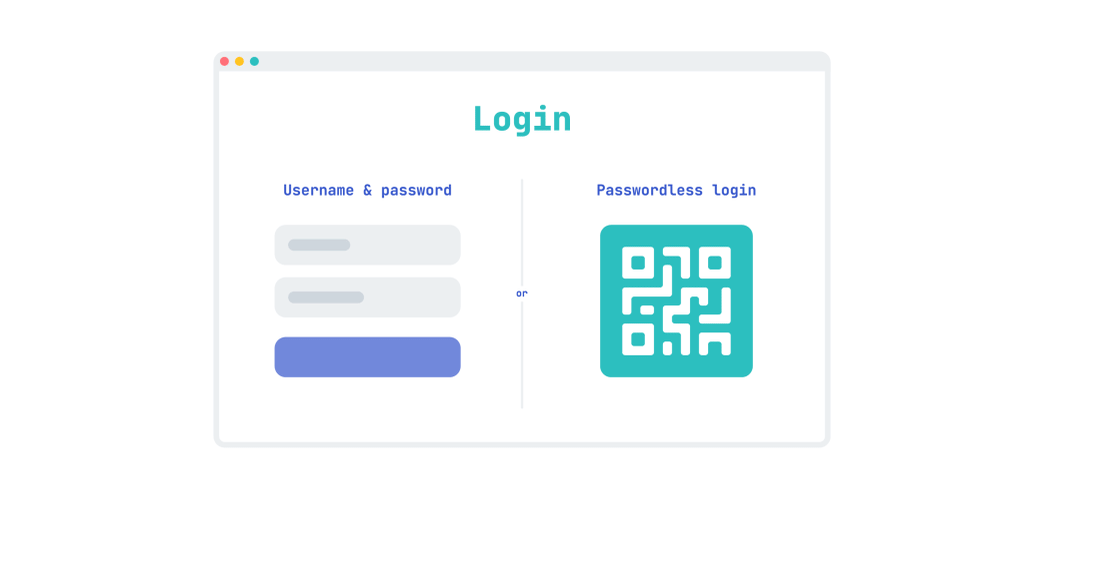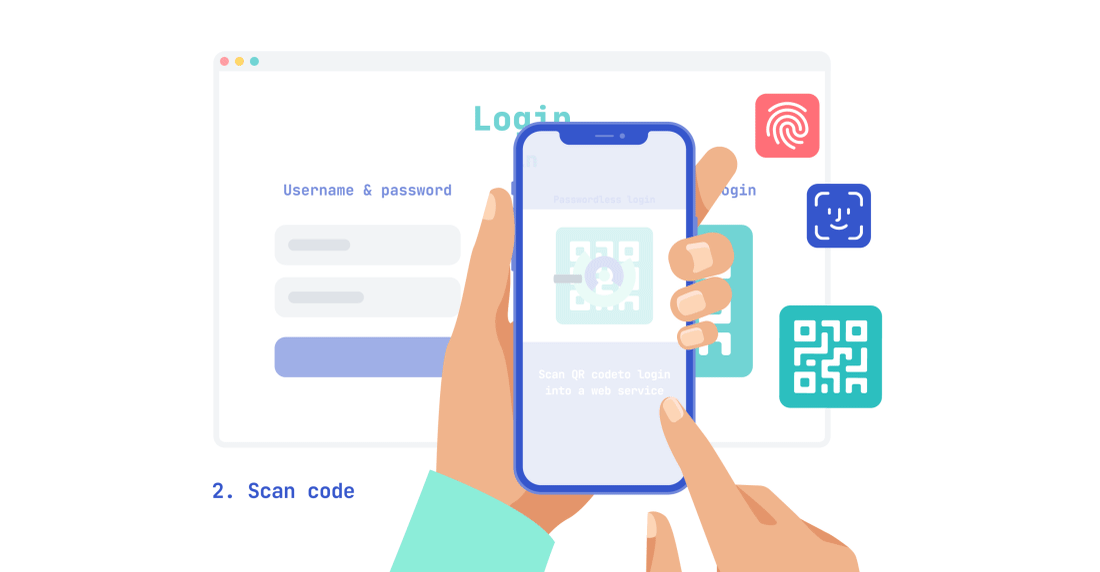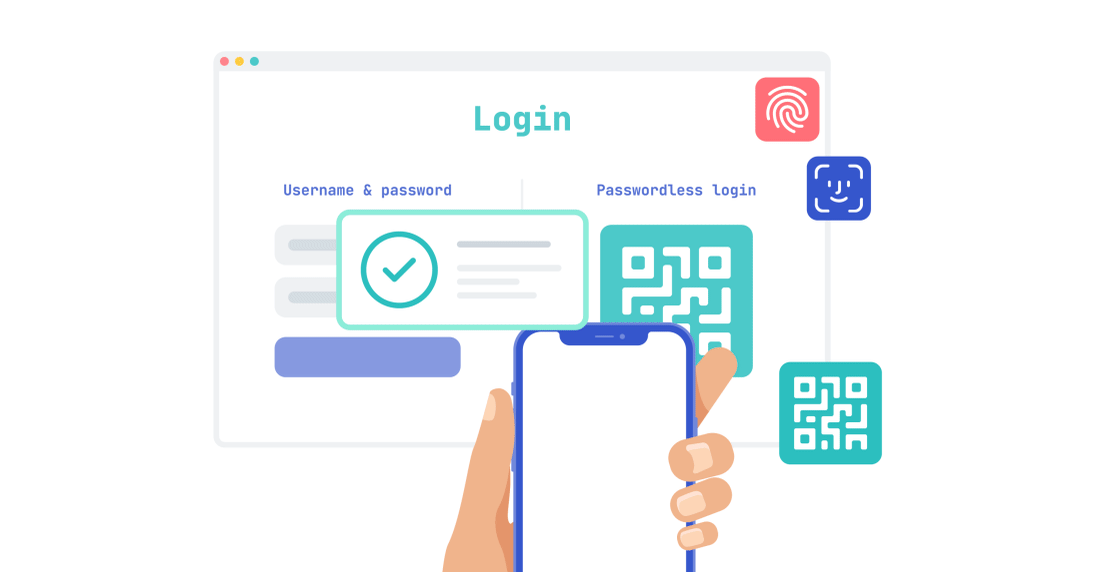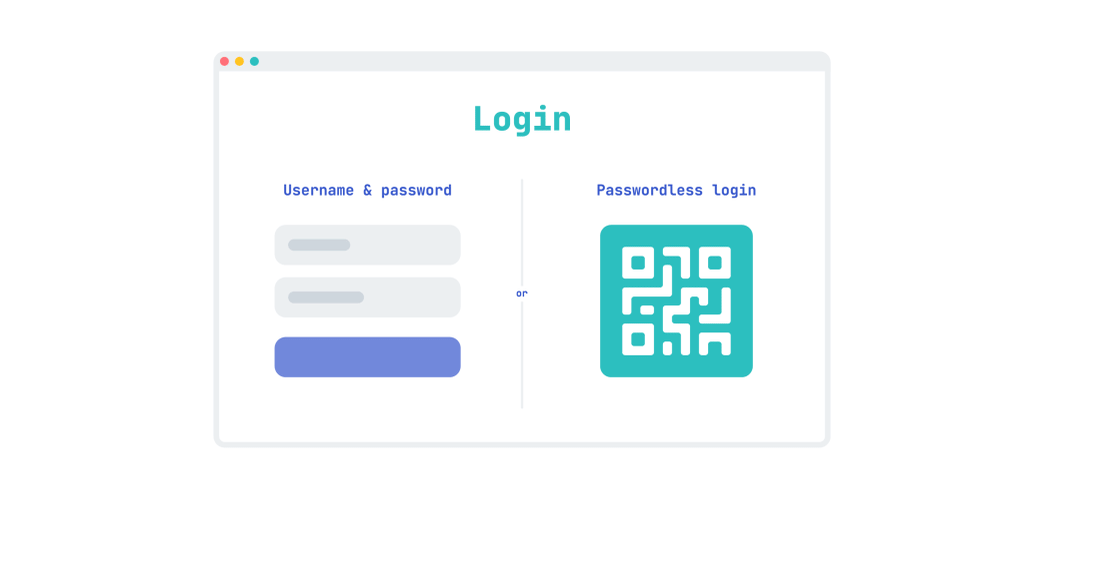
Password-less is an authentication tool that offers users a way to verify themselves while not having to remember or manually type passwords. This leads to the system having a higher...
Enforces your company security policies and Filters malicious traffic in your network. Includes and is not limited to full visibility of all web traffic, anti-virus and advanced malware protection, content...
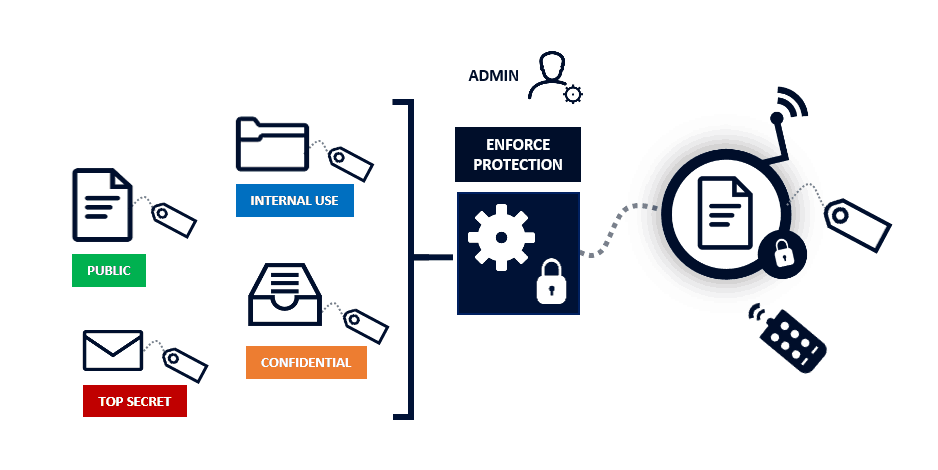
Enterprise Digital Rights Management Protect your trade secrets, intellectual property, and customer data with Enterprise Digital Rights Management Solutions. Our Rights Management is the only browser-based security solution that protects...
Why do you need it? We enable organizations to detect, inspect and secure critical data through our industry‑leading Data Loss Prevention solutions across email, web, and the cloud. How does...
Data Classification simplified with us: Proper visual and metadata labeling of documents and emails Embedded visual markings in the header, footer, and watermark encourage and educate users for proper data...
eMail is no longer a medium of cyberattacks i.e. Phishing but its extended to Phonecalls or now called as Vishing. These forms of social engineering can lead to severe consequences,...
Secure, Simpler, and Safer WAF 3.0 WAF 3.0 is a Distributed proactive web security platform designed to defend against several attacks, including SQL injection, cross-site scripting, and remote file inclusion....
DIGITAL RISK PROTECTION Enterprises are investing in operational capabilities to detect and respond to external threats across the digital risk landscape because the attack surface is not limited to corporate...
- 1
- 2