The importance of cloud security for businesses cannot be overstated.
Cloud Security is the set of policies, procedures, technologies, and policies intended to safeguard Cloud-based environments, systems, applications, and data from unauthorized access, theft, or damage.
As cloud computing services become increasingly popular among businesses of varying sizes, the importance of Cloud Security for organizations that depend on Cloud computing to store and manage sensitive data has become paramount.
At Ambisure Technologies, we understand the importance of Cloud Security for businesses. Our Cloud Security services are designed to protect our clients' Cloud-based systems and data from cyber threats and ensure compliance with industry regulations.
Threats to Cloud Security
Cloud Security threats can take many forms, including malware attacks, phishing scams, data breaches, and DDoS attacks.
Cybercriminals can exploit vulnerabilities in Cloud-based systems to gain unauthorized access to sensitive data, steal intellectual property, or disrupt business operations.
To protect against these threats, businesses must implement robust Cloud Security measures. This includes training employees to identify and avoid phishing scams, using secure passwords and authentication mechanisms, and implementing encryption and other security technologies to protect data in transit and at rest.
Cloud Security Solutions
At Ambisure Technologies, we offer a range of cloud security solutions & services designed to help businesses protect their cloud-based systems & data. Our cloud security solutions
Zero Trust Runtime Security
Automated application hardening for cloud-native applications
Network Segmentation & Firewalling
Easily orchestrate network segmentation & firewalling
Adv Cloud Workload Protection
Protect applications, data, and the network
Multi-Cloud, Multi-Platform Security
Feature flags, rollouts, & A/B tests for developers powered by Full-Stack
Anomaly Detection
Detect and protect against anomalous and malicious behavior
Continuous Compliance
Easily orchestrate network segmentation & firewalling
Vulnerability Scanning
Reduce the risk of critical vulnerabilities in your environment
Personal Data Security
Identify and protect sensitive data in cloud workloads
Business Benefits of Cloud Security
Implementing effective Cloud Security measures can provide numerous benefits for businesses
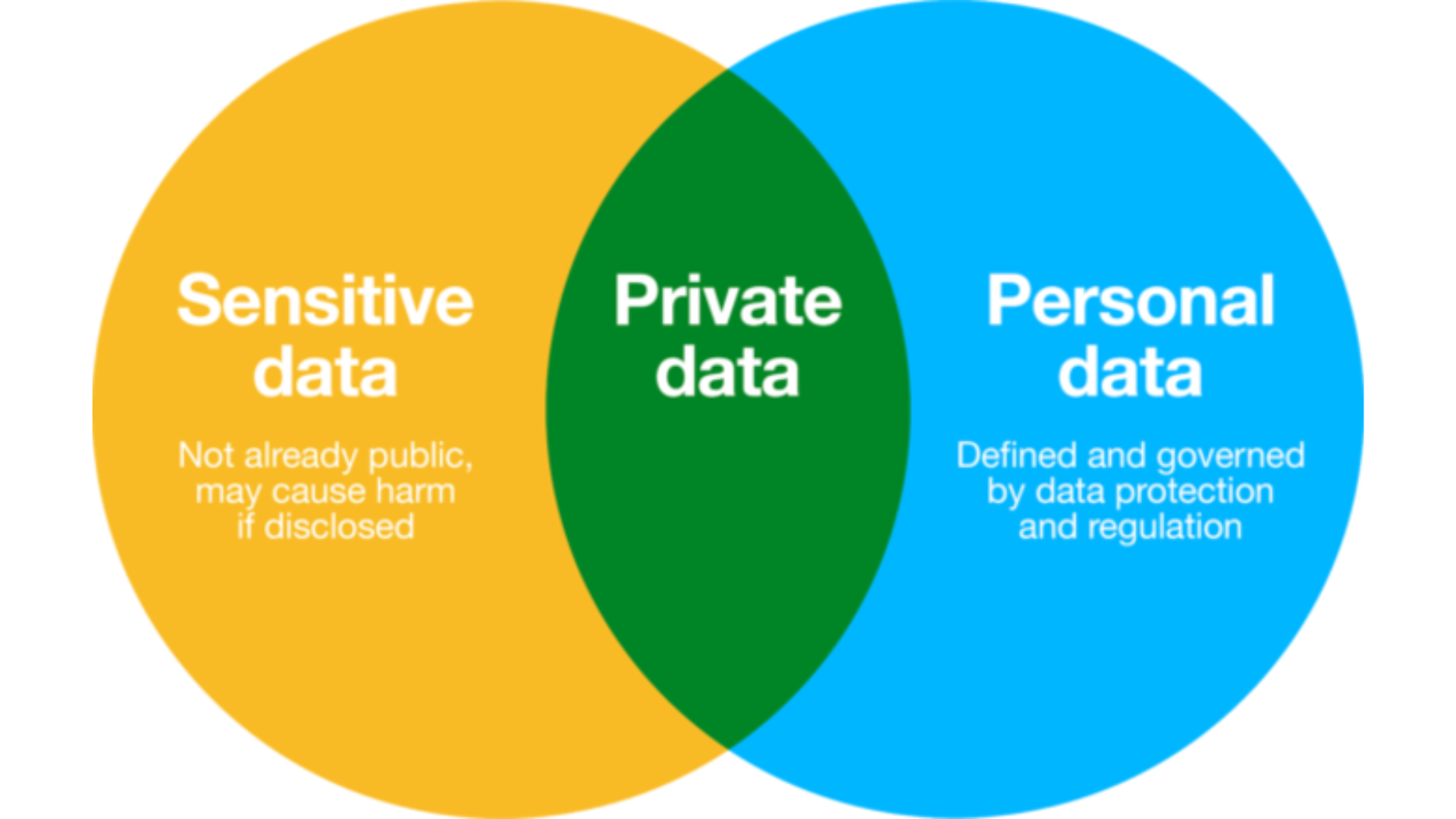
Protecting Sensitive Data
Cloud Security measures can help protect sensitive business data, such as financial information, customer data, and intellectual property, from unauthorized access or theft

Compliance With Regulations
Cloud Security measures can help businesses comply with industry regulations, such as GDPR, HIPAA, and PCI DSS, by ensuring that sensitive data is handled securely and in accordance with regulatory requirements

Collaboration & Productivity
Cloud Security solutions can enable employees to collaborate securely and access data from any location or device, improving productivity and efficiency

Increased Data Availability
Cloud Security solutions can help ensure that business-critical data and applications are always available to authorized users, even during security incidents or disasters

Reduced Costs
Cloud Security solutions can help businesses reduce the costs associated with managing and securing their own IT infrastructure by outsourcing security responsibilities to a trusted third-party provider

Scalability & Flexibility
Cloud Security solutions can provide businesses with the flexibility to scale up or down as needed, allowing them to adjust their security needs as their business grows or changes

SOLUTIONS
Website Security Solutions are
QUERY
frequently asked questions
- Cloud Security refers to the set of policies, technologies, and practices designed to protect cloud-based systems, data, and applications from security threats. As businesses increasingly rely on cloud-based systems for storing and processing their sensitive data, it becomes more critical than ever to ensure the security of these cloud environments.Cloud Security is essential for businesses to protect their sensitive data from unauthorized access, data breaches, and cyber attacks, maintain compliance with industry regulations, and minimize the risk of costly downtime or loss of business-critical data.
There are several common threats to Cloud Security, including unauthorized access, data breaches, cyber attacks, insider threats, insecure interfaces and APIs, and insufficient due diligence by cloud service providers. These threats can compromise the confidentiality, integrity, and availability of cloud-based systems and data, leading to reputational damage, financial losses, and legal and regulatory penalties.
Businesses can take several measures to protect themselves from Cloud Security threats, including:
- Implementing strong access controls and authentication mechanisms to ensure that only authorized users can access cloud-based systems and data.
- Encrypting sensitive data in transit and at rest to prevent unauthorized access or data theft.
- Regularly updating and patching cloud-based systems and applications to address vulnerabilities and prevent exploitation by cybercriminals.
- Using intrusion detection and prevention systems to detect and block malicious traffic.
- Conducting regular security audits and risk assessments to identify and mitigate potential security risks.
- Partnering with a trusted cloud service provider that has robust security measures in place and can provide customized security solutions tailored to the specific needs of the business.
- Educating employees on Cloud Security best practices and the risks of phishing, social engineering, and other forms of cyber attacks.
Businesses can ensure compliance with industry regulations when using Cloud-based systems and data by taking the following steps:
Understand the regulatory requirements: Businesses should have a thorough understanding of the industry regulations that apply to their business and ensure that their Cloud Security solutions and services are designed to meet these requirements.
Choose a cloud service provider that is compliant: Businesses should partner with a cloud service provider that is compliant with industry regulations, such as HIPAA, GDPR, and PCI DSS, and can provide compliance certificates and audits.
Implement appropriate controls: Businesses should implement appropriate controls to protect sensitive data, such as encryption, access controls, and data backup and recovery solutions, to ensure compliance with industry regulations.
Conduct regular compliance audits: Businesses should conduct regular compliance audits to ensure that their Cloud Security solutions and services are aligned with industry regulations and standards.
Train employees on compliance requirements: Businesses should educate their employees on the compliance requirements that apply to their business and provide training on Cloud Security best practices and the risks of non-compliance.
Yes, Cloud Security solutions can help reduce the costs associated with managing and securing a business's IT infrastructure in several ways:
Reduced capital expenditures: Cloud Security solutions typically require lower upfront capital expenditures compared to traditional on-premises solutions, which can help businesses save money on hardware and software costs.
Lower operational costs: Cloud Security solutions can be managed remotely, which can reduce the need for on-site IT staff and lower operational costs associated with managing and maintaining on-premises solutions.
Scalability: Cloud Security solutions can be scaled up or down based on business needs, allowing businesses to only pay for the resources they need and avoid the cost of overprovisioning.
Automatic updates: Cloud Security solutions are typically updated automatically by the cloud service provider, which can save businesses time and money on software updates and maintenance.
Customized solutions: Cloud Security solutions can be customized to meet the specific needs of a business, which can help businesses avoid the cost of implementing unnecessary features or capabilities.