If You Notice One of These Problems
-
 Your website is Blocked
Your website is Blocked
-
 Your website is BlackListed by Search Engine
Your website is BlackListed by Search Engine
-
 You've found strange files what you never uploaded before
You've found strange files what you never uploaded before
-
 Some features are stopped to work on your website
Some features are stopped to work on your website
-
 Noticed strange activity / defacement on the website
Noticed strange activity / defacement on the website
-
 Some files are corrupted or new files are added to you site
Some files are corrupted or new files are added to you site
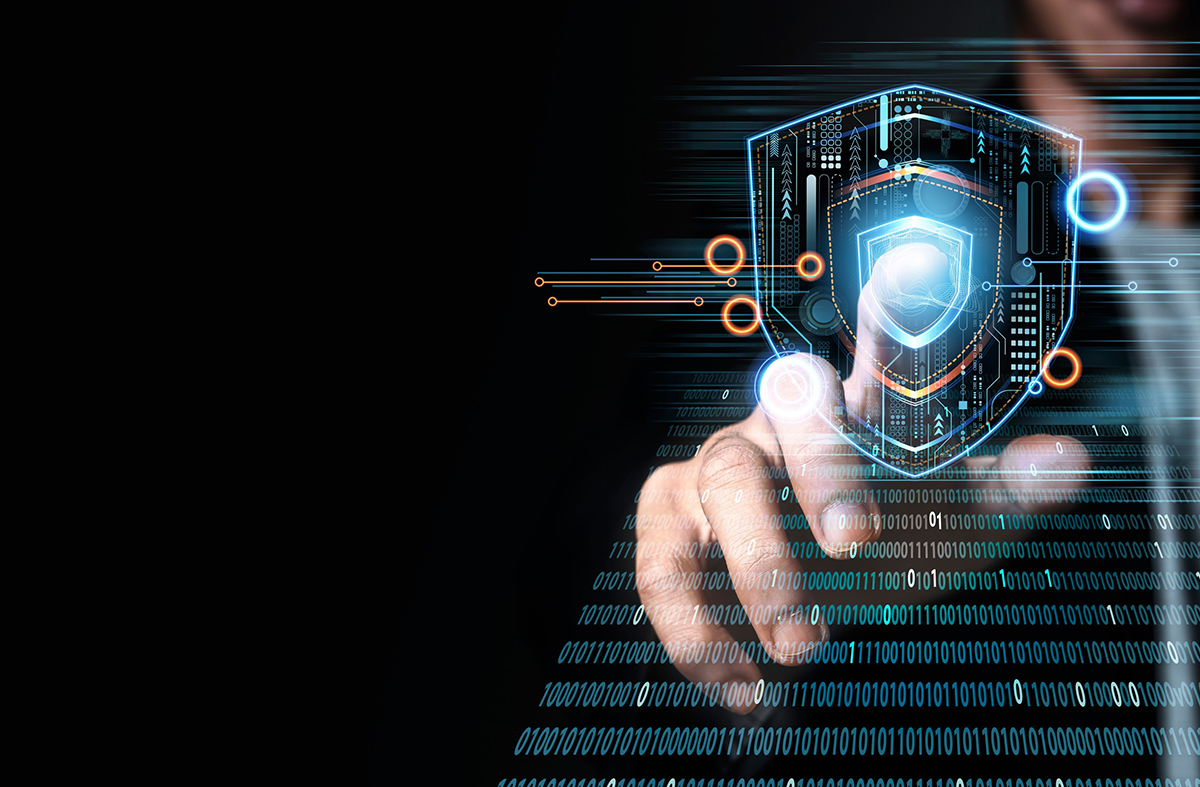
why Need of Security Tools ?
- In order to identify new users, track traffic, approve or deny unauthorized access, and safeguard data and systems from cyberattacks, it is essential to have an authorization and authentication system in place.
- Viruses, spyware, and hackers are a few of the genuine security risks in the online world.
- Every organization needs to be aware of the potentially harmful security assaults and take security precautions.
- Cyber Security Software Tool is required for a company’s or individual’s Security and privacy.
- A method for protecting a network, system, or application from cyberattacks is called cyber security.
- It guards against identity theft, cyberattacks, and data breaches. Some Examples of Security Tools.
- Network Security Monitoring Tool, Web Vulnerability Scanning Tool, Penetration Testing Tool, Cloud Security Tool
What is vulnerability Assessment
A Vulnerability Assessment is a proactive approach to identifying potential security weaknesses and vulnerabilities in an organization’s systems, networks, and applications.
It involves a comprehensive review of the organization’s security posture, including an evaluation of its current security policies, procedures, and technologies.
During vulnerability assessment, security professionals use a variety of tools and techniques to identify and assess potential vulnerabilities. This can include penetration testing, vulnerability scanning, and risk analysis.
During vulnerability assessment, security professionals use a variety of tools and techniques to identify and assess potential vulnerabilities. This can include penetration testing, vulnerability scanning, and risk analysis.
Once vulnerabilities have been identified, the security team can prioritize them based on their severity and potential impact. They can then develop and implement strategies to mitigate or eliminate the vulnerabilities, which may include implementing new security controls, applying patches or updates, or reconfiguring systems and networks.
Security scanning process
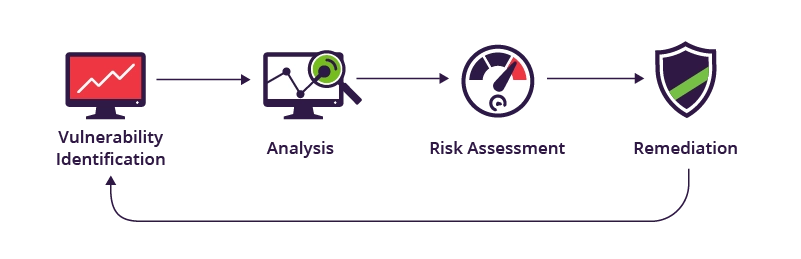

Vulnerability identification

Vulnerability analysis

Vulnerability identification

Remediation
QUERY
frequently asked questions
- Before a new system or application goes live
- When a current system or application is replaced or upgraded
- When a system or application’s remote access requirements or user base changes after previously identified vulnerabilities are remediated (i.e. retest)
- VA typically consists of 1-2 weeks of scanning/testing followed by 1-2 weeks of analysis and report preparation, wait time for VA to start is typically 3-4 months.
- A flaw or weakness in a system that could allow an attacker to compromise the confidentiality, integrity, or availability of the system or data.